For a while, I’ve been manually managing my DNS services in my homelab, and I wanted to document my setup and the lessons I’ve learned along the way to automated. Here’s how I did my DNS updates and why I eventually moved my DNS away from my router.
The Initial Plan
Since my primary router is a MikroTik, and I love how powerful it is, my initial idea was to use MikroTik’s built-in DNS for name resolution.
The plan was simple:
- Manage my DNS records in a Git repository.
- Every time I commit a change to the DNS file, it triggers an Ansible job on my AWX server.
- The job updates the DNS entries on the router automatically.
To make this work, I created an Ansible role, which you can check out here:
👉 GitHub - kr1ps/mikrotik-dns-ansible
The Problem
Everything worked great on my test router, but when I applied the setup to my production router, I ran into an issue:
- The Ansible commands got stuck and timed out after a few seconds/minutes.
- It worked fine on the test router, but that one had very few DNS entries.
- I suspected the timeout was caused by the large number of entries, making requests take longer.
I tried different tweaks mentioned in the official Ansible RouterOS documentation (link ), but in the end, I found that RouterOS wasn’t ideal for automation at this scale.
So, I decided to move DNS services away from the router and manage them separately.
The New Approach
In my homelab, I use my primary domain (kr1ps.com) for both local and external services.
(At some point, I might introduce internal.kr1ps.com for better separation.)
The first DNS solution that came to mind was Bind9. Since I wanted to use the same domain both internally and externally, I needed Bind9’s response-policy feature to handle that logic correctly.
Reliability Matters
Reliability is a top priority. No matter what experiments I run in my homelab, I don’t want to experience interruptions in core services. These include:
✅ Internet
✅ DNS
✅ Home automation
✅ Family password manager
✅ Camera system
✅ WiFi
To ensure rock-solid DNS uptime, I set up two DNS servers:
1️⃣ A Raspberry Pi 5 (4GB RAM) running the primary DNS server, placed right next to my router.
2️⃣ A secondary Linux VM as a fallback.
With this setup, I now have two redundant DNS servers, and my primary DNS is completely standalone. Even if I shut down my homelab servers, WiFi, internet, and DNS will continue running without interruption.
Final Setup
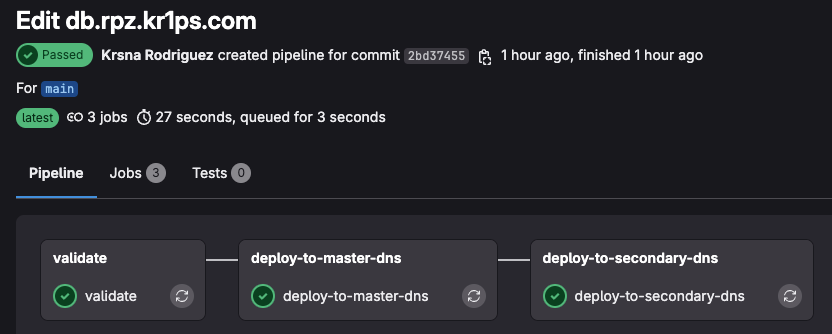
I ended up with a GitLab pipeline that:
- Uses a runner on my network to validate the DNS zone file.
- Once validation passes, it deploys the updated records to their respective servers.
This setup gives me version-controlled DNS, automation through GitLab, and high availability, ensuring that my home network stays stable and responsive. You can check the the code here in this https://sc.coro.net.do/krips/local-dns-mgt
Conclusion
Moving my DNS away from MikroTik gave me better automation, more reliability, and a smoother workflow. If you’re managing your own homelab, I highly recommend separating DNS from your router for more flexibility and scalability.
